Go Config: Stop the Silent YAML Bug (Use mapstructure for Safety)
- October 20, 2025
- Go programming
Go microservices often use YAML, JSON, or TOML for configuration. They are clean, readable, and seems straightforward to load directly into Go structs.
But this common practice harbors a silent, sneaky bug that can allow configuration errors to go undetected during startup, only to crash your app later in production.
The danger? Go’s ‘silent’ zero values. This article shows the danger with a simple, common typo and gives you the safe, robust alternative using the excellent mapstructure library.
The Standard Way: A Silent Killer in Production
Most Go developers use popular libraries for YAML, JSON (e.g., encoding/json), or TOML to load configuration directly into a struct. It’s fast, but here’s where the danger lies.
The Config Setup
Imagine a simple configuration struct:
1type Config struct {
2 ServiceName string `yaml:"service_name"`
3 ListenPort int `yaml:"listen_port"`
4 TimeoutMs int `yaml:"timeout_ms"`
5}
And your configuration file, config.yaml:
1service_name: payment-processor
2listen_port: 8080
3timeout_ms: 5000
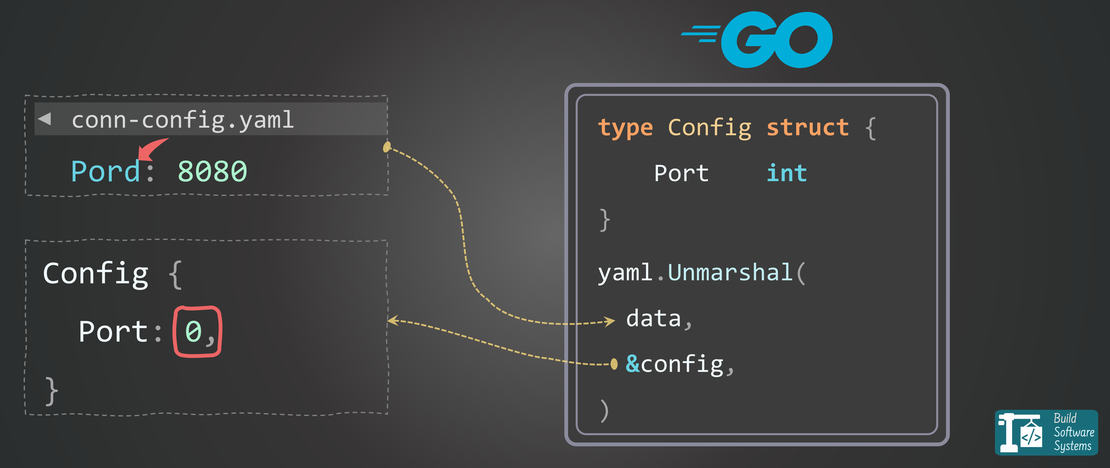
The Zero-Value Trap (The Typo Bug)
Now, imagine a simple typo in your config.yaml:
1service_name: payment-processor
2listen_port: 8080
3timeout_mss: 5000 # 👈 ERROR: Added an extra 's'
If you load this file using a direct YAML library (like those found at https://github.com/go-yaml/yaml or https://github.com/goccy/go-yaml), here’s what happens:
1import (
2 "fmt"
3 "log"
4 "os"
5 "github.com/goccy/go-yaml"
6)
7
8// NOTE: Assume 'data' is read from 'config.yaml' with the typo.
9
10// file read logic
11data, err := os.ReadFile("config.yaml")
12if err != nil {
13 log.Fatalf("Failed to read config file: %v", err)
14}
15
16var cfg Config
17// 👈 Direct unmarshal: The typo 'timeout_mss' is IGNORED here!
18err = yaml.Unmarshal(data, &cfg)
19
20// We skip checking 'err' here because it will be nil, proving the trap.
21// 🚨 The TRAP: err is nil. No error reported!
22fmt.Printf("ListenPort: %d, TimeoutMs: %d\n", cfg.ListenPort, cfg.TimeoutMs)
23// Output: ListenPort: 8080, TimeoutMs: 0
Because Go assigns a zero value (e.g., 0 for int, "" for string, nil for pointers) to struct fields that aren’t present in the YAML, your application loads successfully.
The typo is ignored. But the intended TimeoutMs value is silently set to 0, leading to immediate connection timeouts and misbehavior later in the application’s runtime! You’ve deployed a time-bomb.
The Robust Fix: Introducing mapstructure
To safely load configuration, you need a mechanism that validates the YAML content against your Go struct structure.
The solution is using mapstructure (https://github.com/go-viper/mapstructure), which is designed precisely for robustly converting generic map data into a concrete struct.
1. The Strict Decoding Guardrail
The mapstructure Approach: A Two-Step Firewall
Instead of unmarshaling YAML directly into your struct (which is like handing a key to a stranger), mapstructure creates a firewall.
- The YAML data is first unmarshaled by your chosen YAML library into a generic map (
map[string]interface{}). - It then uses strict validation to ensure every single key in that map has a corresponding field in your struct.
Instead of unmarshaling directly into Config, we first unmarshal the YAML into a generic map, then use mapstructure.Decode to map that data into our struct:
1import (
2 "fmt"
3 "log"
4 "os"
5 "github.com/goccy/go-yaml"
6 "github.com/go-viper/mapstructure/v2"
7)
8
9// Assume: 'config.yaml' contains the typo: timeout_mss: 5000
10data, err := os.ReadFile("config.yaml")
11if err != nil {
12 log.Fatalf("Failed to read config file: %v", err)
13}
14
15// 1. Unmarshal YAML into a generic map
16var tempMap map[string]interface{}
17err := yaml.Unmarshal(data, &tempMap)
18if err != nil {
19 log.Fatalf("Failed to unmarshal YAML to map: %v", err)
20}
21
22var cfg Config
23
24// 2. Configure mapstructure for strict decoding
25decoderConfig := &mapstructure.DecoderConfig{
26 Metadata: nil,
27 Result: &cfg,
28 // 🔥 THE CRITICAL FLAG: This ensures all keys in the map are mapped.
29 // It immediately flags the typo "timeout_mss" as an unused key!
30 ErrorUnused: true,
31}
32decoder, _ := mapstructure.NewDecoder(decoderConfig)
33
34err := decoder.Decode(tempMap)
35// Output with typo: err is NOT nil!
36// Error: "yaml: unknown field "timeout_mss" in config.Config"
The crucial part is setting ErrorUnused: true in the DecoderConfig. This immediately flags the timeout_mss typo as an unused field in the map, turning a silent runtime bug into a clear startup error!
Info
This technique also works great for lists/arrays within your configuration.
2. Handling Complex Types (The Caveat)
One caveat with mapstructure is that it doesn’t automatically handle some complex types that direct YAML libraries do, such as time.Duration.
Because mapstructure is converting a generic map, you often need to register a custom decoder hook to teach it how to convert a string (like "5s") into the specific Go type.
To solve the common time.Duration problem, you can use mapstructure’s powerful built-in hook:
1// Remember to import "time" and "github.com/go-viper/mapstructure/v2"
2
3// Update the decoder config to use the built-in time conversion hook:
4decoderConfig := &mapstructure.DecoderConfig{
5 // ... other config (like ErrorUnused: true) ...
6
7 // 💡 THE SOLUTION: Use DecodeHook to teach mapstructure new conversions.
8 DecodeHook: mapstructure.ComposeDecodeHookFunc(
9 // This built-in function converts strings ("5s") into time.Duration.
10 mapstructure.StringToTimeDurationHookFunc(),
11 // Add your own custom hooks here for other types...
12 ),
13 // ...
14}
This ensures your config can use human-readable duration strings (like listen_timeout: 5s) while still leveraging mapstructure’s safety features.
Final Takeaway: Stop The Silence
Stop relying on Go’s zero values to catch your configuration typos.
By inserting the mapstructure safety layer between your unmarshal step (whether from YAML, JSON, or TOML) and your final struct, you gain compile-time-like validation for your configuration.
Your microservices will be more robust, and you’ll catch configuration errors before deployment.
The takeaway: Always decode config maps using mapstructure with ErrorUnused: true!
Newsletter
Subscribe to our newsletter and stay updated.