Dependency Hell: 5 Strategies to Manage Open Source Risks (The Dependency Dilemma)
- November 17, 2025
- 9 min read
- Programming concepts
Table of Contents
Every developer faces the question: Should I use that third-party library?
The choice saves weeks of time but opens the door to Dependency Hell.
This dilemma is driven by transitive dependencies—the chain of other libraries your chosen package relies on.
This article dives into the problem using a real-world Rust project, sharing the exact clashes and 5 rules to prevent them.
The Rust Project’s Painful Upgrade Journey
I recently experienced this dilemma firsthand while working on a Rust project that involved two main components:
- A utility for starting and managing processes.
- A micro-service connecting to an external REST API (HTTP GET).
To rapidly build the initial software, I chose popular third-party Rust libraries (or crates): psutil for the utility and the widely-used hyper for the REST client.
Everything was smooth until a necessary platform change forced a major update: upgrading the Rust version from 1.74 to 1.80 (a specific constraint due to the target OS, Ubuntu 22.04).
Note
Developers rarely upgrade dependencies just for fun.
The imperative usually comes from the need to fix a critical bug, close a security vulnerability, or access a major performance improvement/new feature offered in the latest release.
This is why neglecting dependencies isn’t an option.
Issue 1: The Breaking API Change (Hyper v1.0)
I decided to upgrade my dependencies simultaneously. This is where the trouble started. The latest stable version of hyper (v1.0) had drastically restructured its API, removing the “batteries-included” functionalities for easily creating clients and servers.
The Takeaway: The shift to a stable version (
v1.0) can sometimes mean a breaking change that requires significant code rework. Even stable libraries can change their core philosophy.
Issue 2: The Deep Dependency Clash
To avoid a massive rewrite of my client logic, I decided to switch to the higher-level (easier to use), more feature-rich reqwest crate.
I chose reqwest because it is one of the most popular and well-maintained HTTP clients in the Rust ecosystem, and it conveniently wraps hyper, abstracting away its complexity.
This move immediately led to a dependency clash:
The issue centered on the low-level memchr crate.
The older psutil package, through its dependency chain (specifically via the darwin-libproc crate), explicitly locked the required version of memchr to the older 2.3.0 release.
Meanwhile, the newer reqwest package required a later version (^2.4.1).
Since Rust’s build system, Cargo, cannot use two different versions of the same crate in the final build (a fundamental limitation known as the Dependency Hell problem), the compilation failed.
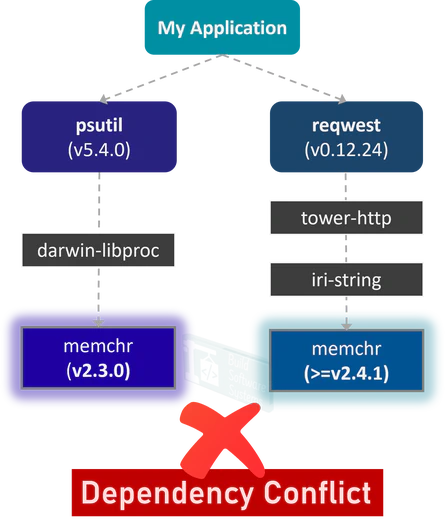
The specific clash was between the psutil dependencies and the reqwest crate when it was at version 0.12.24. This forced me into a painful downgrade cycle.
To get the project compiling, I was forced to downgrade reqwest to satisfy the older version of the psutil dependency.
For context, here are the problem configurations that revealed the clash:
psutilversion:5.4.0reqwestversion:0.12.24- Rust compiler version:
1.80.1
`cargo build` output error (Issue 2)
error: failed to select a version for `memchr`.
... required by package `iri-string v0.7.0`
... which satisfies dependency `iri-string = "^0.7.0"` of package `tower-http v0.6.6`
... which satisfies dependency `tower-http = "^0.6.5"` of package `reqwest v0.12.24`
... which satisfies dependency `reqwest = "^0.12.24"` of package `myproject v0.1.0 (/myproject)`
versions that meet the requirements `^2.4.1` are: 2.7.6, 2.7.5, 2.7.4, 2.7.3, 2.7.2, 2.7.1, 2.7.0, 2.6.4, 2.6.3, 2.6.2, 2.6.1, 2.6.0, 2.5.0, 2.4.1
all possible versions conflict with previously selected packages.
previously selected package `memchr v2.3.0`
... which satisfies dependency `memchr = "~2.3"` of package `darwin-libproc v0.2.0`
... which satisfies dependency `darwin-libproc = "^0.2.0"` of package `psutil v5.4.0`
... which satisfies dependency `psutil = "^5.4.0"` of package `myproject v0.1.0 (/myproject)`
failed to select a version for `memchr` which could resolve this conflict
This shows how even a single direct dependency like psutil can bring in many transitive requirements, dramatically increasing the surface area for trouble.
Running cargo tree on a simple dependency like psutil often reveals dozens of nested, transitive dependencies, dramatically expanding the risk of a clash like the one we saw with memchr
For example, `cargo tree -p psutil`
psutil v5.4.0
|-- cfg-if v1.0.4
|-- derive_more v1.0.0
| `-- derive_more-impl v1.0.0 (proc-macro)
| |-- proc-macro2 v1.0.103
| | `-- unicode-ident v1.0.22
| |-- quote v1.0.42
| | `-- proc-macro2 v1.0.103 (*)
| `-- syn v2.0.110
| |-- proc-macro2 v1.0.103 (*)
| |-- quote v1.0.42 (*)
| `-- unicode-ident v1.0.22
|-- glob v0.3.3
|-- nix v0.30.1
| |-- bitflags v2.10.0
| |-- cfg-if v1.0.4
| `-- libc v0.2.177
Issue 3: The Compiler Version Barrier
Just when I thought I was in the clear, another issue appeared: some dependencies buried deep in the reqwest dependency tree required Rust 1.83 and more.
`cargo build` output error (Issue 3)
error: rustc 1.80.1 is not supported by the following packages:
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.83
[email protected] requires rustc 1.82
[email protected] requires rustc 1.82
[email protected] requires rustc 1.82
[email protected] requires rustc 1.82
[email protected] requires rustc 1.82
[email protected] requires rustc 1.82
[email protected] requires rustc 1.81
[email protected] requires rustc 1.82
[email protected] requires rustc 1.82
Either upgrade rustc or select compatible dependency versions with
`cargo update <name>@<current-ver> --precise <compatible-ver>`
where `<compatible-ver>` is the latest version supporting rustc 1.80.1
I was forced to downgrade those dependencies, too.
The only viable path forward without delaying the project for weeks was to accept a painful compromise: I locked the project to older, known-working versions of both reqwest and psutil that satisfied their conflicting transitive requirements.
This compromise allowed the project to compile on Rust 1.80 but meant sacrificing newer features and stability updates from the latest library versions.
This entire process—spent juggling dependency versions instead of writing application logic—is the perfect illustration of the dependency dilemma.
If you’ve been in this situation before, tell us in the comments how you would have tackled the deep dependency clash and the compiler version barrier!
The Core Question: Is Self-Implementation Better?
After a long, frustrating time spent debugging Cargo.lock and Cargo.toml files, I asked the fundamental question: Wouldn’t it just be better to self-implement these simple functionalities?
The truth is, development is great until the day you need to upgrade, patch a security vulnerability, or add a new feature.
Then, that initial time saved turns into days of painstaking work in dependency hell.
| Criteria | Third-Party Libraries | Self-Development | Key Insight |
|---|---|---|---|
| Development Time | WIN (Fast Start) | LOSE | The biggest immediate advantage. |
| Code Sharing/Knowledge | WIN (Community) | LOSE | Audited by Community (Safer code). |
| Maintenance Workload | WIN (Externalized) | LOSE | You don’t manage the core library code. |
| Control/Customization | LOSE (Limited) | WIN | Full Control (Easier to patch/customize). |
| Compatibility/Upgrades | LOSE (High Risk) | WIN | Zero Clash Risk (Predictable upgrades). |
| Security Patching | Risk Exposure (Depends on maintainer) | WIN (Immediate control) |
Navigating the Dependency Minefield: Best Practices
The choice between a third-party crate and a custom implementation is rarely a simple “yes” or “no”—it depends. The goal is to maximize the speed and quality benefits of open source while minimizing the risk of dependency friction.
Here are five key insights to help you manage the software dependency dilemma:
1. Demand Stability: Look for v1.0+ (and SemVer)
Always prioritize libraries that adhere to Semantic Versioning (SemVer), especially those at version 1.0.0 or higher.
What is SemVer? It defines version numbers as MAJOR.MINOR.PATCH (e.g., 2.1.5).
- MAJOR bumps (like going from
1.xto2.0) indicate breaking changes that require code updates on your side. - MINOR bumps (
1.1to1.2) add new features but maintain backward compatibility. - PATCH bumps (
1.1.1to1.1.2) are for bug fixes and security patches.
By choosing a library that has committed to SemVer 1.0+, you gain a crucial promise: Breaking API changes will only happen on major version updates. This predictability is your first defense against Dependency Hell.
The Rule: Avoid pre-1.0 libraries unless they are absolutely essential, and if used, isolate them completely (see Point 2).
2. Create an Abstraction Layer (The Buffer Zone)
Create a clean boundary, or an abstraction layer, between your core application logic and the third-party library.
If you use reqwest for HTTP requests, wrap it in your own small HttpClient module. If you ever have to switch to hyper or a different HTTP client, you only need to update the logic inside that single module, not scattered throughout your entire codebase.
3. Check Health: Maintenance, Usage, and the Dependency Tree
Perform due diligence. Before adopting a new dependency, check:
- Maintenance Status: How recent are the last few commits?
- Usage: How many other major projects rely on it?
- Dependency Count: Check the dependency tree to see if it relies on a massive, complex web of other dependencies. Prioritize libraries with fewer, more established dependencies.
4. Decouple Upgrades: Compiler First, Dependencies Second
Wait until you can upgrade your language/compiler version (e.g., Rust 1.83) before you attempt a major dependency upgrade.
While this means you might miss out on a few minor new features, it ensures you have the necessary platform to support the updated libraries without forcing painful downgrades.
5. Build vs. Buy: When to Fork or Self-Implement.
- Lagging Dependencies: If a dependency of your dependency is abandoned, consider submitting a Pull Request (PR) to update it yourself, or creating a fork if time is critical.
- Simple Logic: If a library’s functionality is non-core, specific to your needs, and relatively simple (e.g., a simple file parser, basic CLI argument handling), it’s often safer to implement it yourself to retain full control and avoid unnecessary external requirements.
Newsletter
Subscribe to our newsletter and stay updated.
Conclusion: The Core Trade-Off
The Software Dependency Dilemma is the eternal trade-off between Velocity (Time-to-Market) and Stability (Long-Term Maintainability).
Be strategic: Isolate your libraries, vet their health, and own simple logic. This discipline is the only path to building resilient software without the deep friction of Dependency Hell.
Newsletter
Subscribe to our newsletter and stay updated.