C++ Heap Memory Pitfall: Why Returning Pointers Can Break Your Code
- June 29, 2025
- 7 min read
- C++ programming
Table of Contents
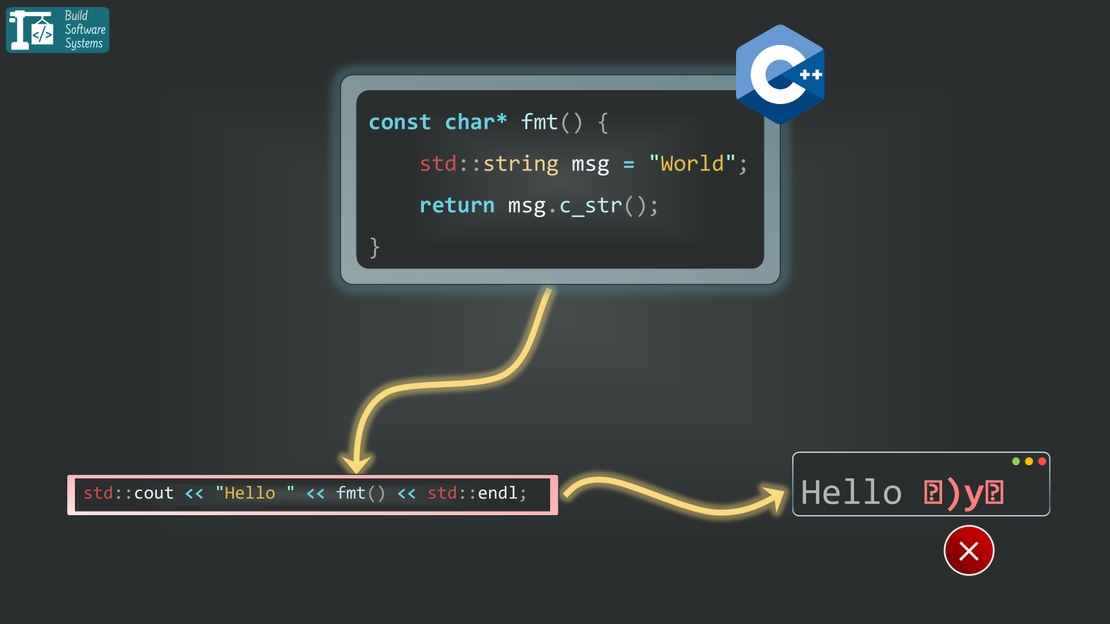
Not long ago, I was knee-deep in a debugging session, staring at a strange log line that made no sense:
# Formatted Obj: �)y�
At first, I assumed a logging bug or encoding issue. But tracing it back led to a seemingly harmless C++ function:
1const char* fmt() {
2 std::string msg = "error message (error code)";
3 return msg.c_str(); // 😱 Uh-oh...
4}
Yes — it returns c_str() on a local std::string. And just like that, a classic C++ pitfall causes garbage to leak into logs. The worst part? It compiles just fine. No crash, no compiler error — just broken output.
Even experienced C++ developers sometimes fall into this trap. But why is this such a subtle and dangerous issue?
Let’s break it down.
What’s Going Wrong?
Let’s look at a more realistic version of the function:
1#include <iostream>
2#include <string>
3
4struct Object {
5 std::string firstName;
6 std::string lastName;
7
8 const char* fmt() {
9 std::string msg = "{\n";
10 msg += "\t\"firstName\": \"" + firstName + "\",\n";
11 msg += "\t\"lastName\": \"" + lastName + "\"\n";
12 msg += "}";
13 return msg.c_str(); // 😬 Dangerous
14 }
15};
16
17int main() {
18 Object obj = {"John", "Doe"};
19 std::cout << "Formatted Obj: " << obj.fmt() << std::endl;
20 return 0;
21}
At first glance, this seems reasonable: build a JSON string, return its C-style representation. But this returns a pointer to memory that becomes invalid the moment the function ends.
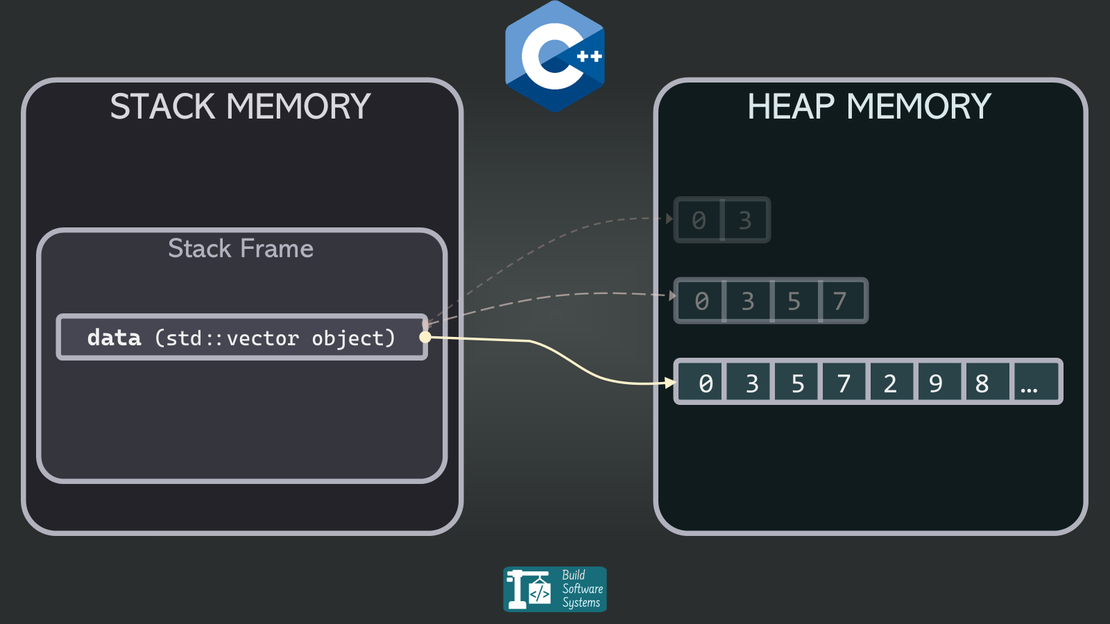
Even though the buffer lives on the heap, its lifetime is tied to the std::string on the stack. Once that’s gone, so is the buffer.
What’s Actually Happening in Memory
Here’s a quick breakdown of typical memory layout in a C++ program:
| Memory Area | Purpose | Lifetime |
|---|---|---|
| Stack | Function frames, local variables | Auto-managed, cleared on return |
| Heap | Dynamically allocated memory | Until delete / free |
| Data Segment | Global/static variables | Entire program lifetime |
| Text Segment | Executable code | Static, read-only |
More details in my article on process creation from executable.
So in our example:
msgis a local variable — it lives on the stack.- Its internal buffer (via
c_str()) is on the heap, but is managed bystd::string. - When the function returns,
msgis destroyed, which frees that heap memory. - Returning
msg.c_str()returns a pointer to memory that’s now invalid.
It doesn’t matter that the buffer was on the heap. The ownership was on the stack, and once that’s gone, the buffer is invalid.
Accessing that pointer — reading, printing, or copying — results in behavior that’s unpredictable and unsafe.
Note
While this example uses std::string, the same danger applies to many STL containers like std::vector, std::array, and even custom data structures that expose raw pointers to their internal buffers.
For instance:
1const int* getData() {
2 std::vector<int> v = {1, 2, 3};
3 return v.data(); // ❌ Same mistake: pointer to destroyed buffer
4}
Why This Is So Dangerous
- The pointer looks valid — it’s not
nullptr. - The contents may still seem correct, especially if no other operation has reused that memory.
- But this leads to erratic, platform-dependent behavior: sometimes valid output, sometimes corrupted text like
�)y�, or even a crash.
Depending on compiler and platform:
std::cout << obj.fmt()may appear to work if the memory hasn’t been reused yet.- On another run or machine, it might print garbage.
- Replacing
std::coutwithprintf("%s\n", obj.fmt())might even appear more stable — but that’s just an illusion. You’re relying on memory that hasn’t been overwritten yet, which can change unpredictably depending on the platform, compiler, or even unrelated changes in your code.
The danger is in the illusion of safety — that “it works sometimes” hides a bug that can strike later and harder.
What Can Go Wrong?
Returning a pointer to a destroyed local string might seem harmless — until it’s not. Here are potential outcomes:
- Silent data corruption (e.g., garbled logs)
- Application crashes
- Security risks from use-after-free vulnerabilities
- Inconsistent behavior that varies across builds or executions
It’s one of those classic C++ bugs: it compiles, and might even “work”… until it doesn’t.
Safer Alternatives: Do It Right
1. Return std::string by value
Let the compiler handle memory. Modern C++ uses Return Value Optimization (RVO) and move semantics to make this efficient.
1std::string fmt() {
2 std::string msg = "{\n";
3 msg += "\t\"firstName\": \"" + firstName + "\",\n";
4 msg += "\t\"lastName\": \"" + lastName + "\"\n";
5 msg += "}";
6 return msg; // Safe
7}
And in main():
1std::string msg = obj.fmt();
2std::cout << "Formatted: " << msg << std::endl;
Clean. Fast. Safe.
2. Use a Static Variable (Rarely Recommended)
1const char* fmt() {
2 static std::string msg;
3 msg = "{...}";
4 return msg.c_str(); // OK, msg lives forever
5}
Warning
- Not thread-safe
- Reuses the same memory on each call
- Can lead to hard-to-trace bugs due to shared state
3. Manually Allocate a Buffer (C-style)
1char* fmt() {
2 std::string temp = "{...}";
3 char* buffer = new char[temp.size() + 1];
4 std::strcpy(buffer, temp.c_str());
5 return buffer;
6}
But now you’re responsible for calling delete[]. Error-prone and outdated. If you must, prefer using the unique_ptr smart pointers to manage memory automatically:
1std::unique_ptr<char[]> fmt() const {
2 std::string msg = "{...}";
3 std::unique_ptr<char[]> buffer(new char[msg.size() + 1]);
4 std::strcpy(buffer.get(), msg.c_str());
5 return buffer;
6}
4. Pass a buffer into the function
1void fmt(char* buffer, size_t bufferLen) {
2 std::string msg = "{...}";
3 std::snprintf(buffer, bufferLen, "%s", msg.c_str());
4}
Usage:
1char buffer[256];
2obj.fmt(buffer, sizeof(buffer));
3printf("Formatted: %s\n", buffer);
This approach is safer for C interoperability.
Warning
Drawback: if the message is too long, it will be truncated.
Catching These Bugs Early
Use Compiler Warnings
Enable aggressive flags:
1g++ -Wall -Wextra -Wreturn-stack-address your_file.cpp
With Clang, you might get:
warning: address of stack memory associated with local variable 'msg' returned
Use Runtime Tools
-
AddressSanitizer (
-fsanitize=address) — best-in-class tool for catching use-after-free. -
Valgrind — slower, but powerful for memory analysis.
-
Static analyzers — like Clang Static Analyzer or cppcheck.
Minimal Repro: Try It Yourself
1#include <iostream>
2#include <string>
3
4const char* getDangerous() {
5 std::string msg = "Hello!";
6 return msg.c_str();
7}
8
9int main() {
10 const char* ptr = getDangerous();
11 std::cout << ptr << std::endl; // May print "Hello!"... or garbage
12}
Try this with and without sanitizers. You’ll often get “Hello!” — but it’s still unsafe.
You may also replace the std::cout statement with printf("%s\n", ptr); to see how it might appear to work, but it’s still undefined behavior.
Newsletter
Subscribe to our newsletter and stay updated.
Conclusion
C++ gives you power, but also responsibility. Returning pointers to memory managed by local objects — even if the memory is on the heap — can break your code in unpredictable ways.
Even seasoned developers sometimes make this mistake, especially under pressure or in legacy codebases.
So if you ever see garbled logs like �)y�, don’t ignore it. It might be your program’s way of saying:
“You’re using memory that no longer exists.”
Are you learning C++? Check out this curated list of resources and coding conventions here.